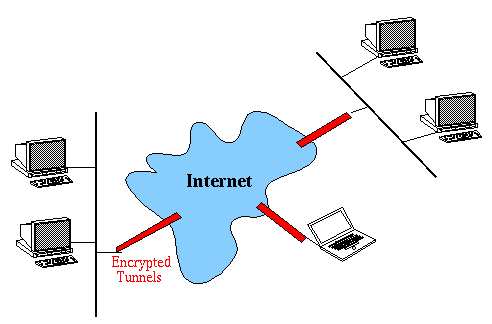
Virtual Private Networks
Virtual private networks (VPN) provide an encrypted connection
between a user's distributed sites over a public network (e.g., the Internet).
By contrast, a private network uses dedicated circuits and possibly
encryption.
This page describes IP-based VPN technology over the Internet,
though an organization might deploy VPN's on its internal nets (
intranets)
to encrypt sensitive information.
We also have some performance numbers.
The basic idea is to provide an encrypted IP tunnel through the Internet
that permits distributed sites to communicate securely.
The encrypted tunnel provides a secure path for network applications
and requires no changes to the application.
Design Issues
- supported platforms (UNIX, Win*, Mac)
- proprietary or open solution (standards support)
- ease of use (end user and network manager/SNMP)
- performance (pkts/sec, encryption bandwidth, compression)
- IP fragmentation support
- strength of security
- firewall inter-operability
- features (firewall, addressing, IPv6 support, protocols, multicast)
- network address translation (NAT) for host and client
- mobile user support
- key and policy management, authentication
- scalability
- export restrictions
- internals (chipset, MHz, memory, net interfaces, tamper resistance)
- cost
Software solutions
- The software solutions might be better termed "software approximations."
The classic solution is to provide privacy on an application-by-application
basis using
crypto APIs.
Secure remote access is provided by encrypted telnet services
like SRP
or SSH.
SSH also permits tunneling other services (like X) over the
encrypted connection.
For dial-in connections, Blaze's
Encrypting Session Manager (ESM) provides encryption
after the session has been established.
Encrypted voice communication over the Internet is provided by
Nautilus or
PGPfone.
Transport layer encryption for TCP is provided by
SSL,
also see the IETF's
Transport Layer Security (TLS) drafts.
More integrated software solutions can be provided by
Kerberos
or OSF's
DCE
or by using a Point to Point Tunnelling Protocol
(PPTP
or Microsoft's
PPTP implementation
and a FAQ)
and vulnerabilities.
L2TP
combines the best of PPTP and Cisco's
L2F protocol.
-
Blaze's swIPe,
or vpnd,
and CIPE
provide encrypted transport services, also see Gong's
enclave paper.
The on-going development of
IP security options for IPv4 and IPv6 along with ISAKMP and GKMP
may soon provide the necessary software tools for constructing your
own virtual private network, and there are
some
implementations available for testing, also see
paper
on MS-DOS implementaton.
Also, see the recent
Internet draft,
or the VPN framework, or the
S/WAN initiative
and Linux freeswan or
or OpenVPN
NIST's cerberus.
Commercial solutions
- InternetWeek's vpn
page
- DataComm's tests 7/98
- LANtimes review of VPN's (10/98)
- Network Computing
VPN review (9/98)
and IPsec VPNs 9/99
- Cisco's
IOS security architecture and
Cisco's PIX info
- DSN's NetFortress
or here
- Brivida's Pirma One
- DEC's
altavista tunnel and a comparison
- VPlus Networks
- InfoExpress
VTCP/Secure
- IBM's SecureWay
- compatible systems
- shiva vpn
- redcreek VPN hardware for NT
- Xerox Ethernet tunnel
- Bay/New Oak NOC 4000
or here
- Microsoft's Windows 2000 VPN
- Shiva infocrypt
- NEC's PrivateNet
- NetLOCK
or here
and a review
- aventail
and their
white papers
- IRE's SafeNet
or firstvpn.com
- Radguard's CiPro and a
review
- Cylink's
SecureDomain
- DataFellows
F-Secure VPN
- Win* solutions:
Secure Client
or Ashley Laurent VPCOM
or SKIP
- NSC/StorageTek
BorderGuard
- Checkpoint's Firewall-1 vpn
- blueridgenetworks.com
- Some
firewall vendors and (soon)
router vendors provide VPN services, e.g., see
Cisco's encrypting routers
- vpnlabs info
- Timestep's
IPsec whitepaper
- more
VPN info and links/FAQ
-
vpn references and links
Test and evaluation
- The
Network Research Group at
ORNL has been doing
evaluations of various VPN solutions, including STEL, SSH, Kerberos,
DCE, ESM,
and IPv4/v6 with Cisco ISAKMP daemon.
We have also done preliminary testing on Cisco PIX unit, DEC's
AltaVista client tunnel, and DSN's NetFortress.
Here are some
preliminary performance data
of encrypted tunneling throughput and latency.
Last Modified thd@ornl.gov
(touches: )
Other security related links can be found
here.
back to Tom Dunigan's page
or the ORNL home page

